

Lately it seems like not a day goes by without news that a well-known female celebrity has been the victim of a photo hack—Emma Watson, Demi Lovato, and Amanda Seyfriend in the past month alone. It's a profoundly depressing, gross, and sexist situation.
"Taking a picture of your naked body is not an abnormal or immoral thing to do, and it certainly shouldn't be a forfeiture of privacy."
Too often, the narratives surrounding these leaks point blame—even just subtly—at the victims, as if it's somehow wrong (or even remotely abnormal) to have nude pictures on your phone. For the record, it's not.
Taking a picture of your naked body isn't an abnormal or immoral thing to do, and it certainly shouldn't be a forfeiture of privacy. In fact, blaming the victims of photo hacks for the violation of their own privacy is absurd—as it implies that having a body (and the audacity to love and celebrate that body) is inherently wrong. It also implies that innocent people should police their private, harmless behavior instead of focusing on the fact that criminals shouldn't commit crimes.
But this is the world we live in. A world where privacy is a right that's frequently violated, and in which people—especially young women—are targeted explicitly.
In the case of celebrity hacks, the way in has typically been iCloud. This was the case in 2014's infamous "Fappening" hack, in which nude photos of stars like Jennifer Lawrence, Kate Upton, and Kirsten Dunst were stolen and leaked. While it's not clear yet just how the latest round of hacks were executed, the cloud is a likely culprit.
So how do you protect yourself from a cloud-based photo hack? Here are a few steps you can (and should) take.
1. Review your cloud storage settings—and know what they mean.
Whether you're an iPhone or Android user, your photos may be automatically saving to the nebulous "cloud." Check your settings to make sure you haven't been opted into cloud storage without realizing it.
Stay In The Know
Marie Claire email subscribers get intel on fashion and beauty trends, hot-off-the-press celebrity news, and more. Sign up here.
On iPhone, go to Settings > iCloud > Photos. Within the Photos tab, you'll have the option to turn on or off three different iCloud photo services: iCloud Photo Library, My Photo Stream, and iCloud Photo Sharing. Read the descriptions of each carefully, and decide if you're comfortable opting in.
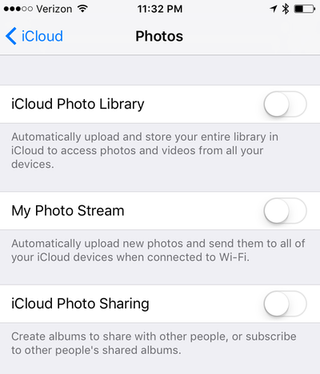
On Android devices, open the Google Photos app and tap the menu icon in the top left corner. From there, go to Settings > Back up & sync, and turn the feature off if you don't want your photos automatically backed up in your Google account.
2. Check your cloud storage account online to see what's in there.
Sign in to your iCloud or Google Photos account online to see which of your photos (if any) have been automatically backed up, and delete anything you don't want living online.
3. Use password best practices.
Passwords are a pain—and increasingly so in a time when we're starting to use our fingerprints to unlock phones and approve app purchases. But they're a necessary evil, and easy passwords make you vulnerable. Choosing to use a weak password is like choosing to close your door but not lock your deadbolt.
We all know the rules of strong passwords—they should be long (preferably 12 characters or longer—we know); they should contain a mix of upper and lowercase letters, numbers, and special characters; and they shouldn't be obvious, meaningful words (like the pet names and birthdays—or even real words, if you can avoid it).
In addition to crafting strong passwords, you should use a different password for every account, and change your passwords frequently (every 10 weeks is ideal).
4. Consider enabling two-factor authentication.
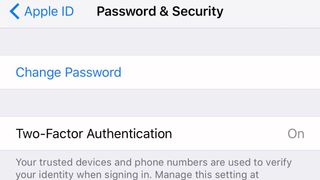
There's a good chance two-factor authentication (2FA) is the bane of your work-password existence, but there's a good reason many companies require it. As its name suggests, 2FA adds a second step to your log-in process and a second layer to your account security.
In addition to entering a username and password, users with 2FA are required to enter an additional piece of information, often a unique code that generates with each log-in attempt. The second code is frequently sent to users via text or generated in an app on their smartphone.
Protect yourself and your friends—share this story with anyone you think might need it.

Kayleigh Roberts is a freelance writer and editor with more than 10 years of professional experience. Her byline has appeared in Marie Claire, Cosmopolitan, ELLE, Harper’s Bazaar, The Atlantic, Allure, Entertainment Weekly, MTV, Bustle, Refinery29, Girls’ Life Magazine, Just Jared, and Tiger Beat, among other publications. She's a graduate of the Medill School of Journalism at Northwestern University.
-
 Olivia Rodrigo Finds the Perfect Spring Dresses at Reformation
Olivia Rodrigo Finds the Perfect Spring Dresses at ReformationShe's worn the brand twice in the past week.
By Julia Marzovilla Published
-
 Curiously, Just as Meghan Markle Sends Samples of Her New Strawberry Jam Out, the Buckingham Palace Shop Starts Promoting Its Own Strawberry Jam on Social Media
Curiously, Just as Meghan Markle Sends Samples of Her New Strawberry Jam Out, the Buckingham Palace Shop Starts Promoting Its Own Strawberry Jam on Social MediaThe clip promoting the Buckingham Palace Shop’s product—we cannot make this up—is set to Mozart’s “Dissonance Quartet.”
By Rachel Burchfield Published
-
 Zendaya's Latest 'Challengers' Serve Is Nearly a Century Old
Zendaya's Latest 'Challengers' Serve Is Nearly a Century OldThe 1930s-era dress may have been pulled months ago.
By Halie LeSavage Published
-
 48 Last-Minute Father's Day Gifts to Scoop Up
48 Last-Minute Father's Day Gifts to Scoop UpHe'll never even know you left it until now.
By Rachel Epstein Published
-
 16 Gifts Any Music Lover Will Be Obsessed With
16 Gifts Any Music Lover Will Be Obsessed WithAirPods beanies? Say less.
By Rachel Epstein Published
-
 This Pet Food Dispenser Is a Game-Changer for My Pet
This Pet Food Dispenser Is a Game-Changer for My PetThe futuristic-looking Petlibro Granary makes me feel so much less guilty being away from my dog.
By Cady Drell Published
-
 The Privacy Whisperers
The Privacy WhisperersYou've read about their companies in the news. Now, hear from the women behind data privacy at the tech industry's heaviest hitters—Facebook, Apple, Google, and more.
By Colleen Leahey McKeegan Published
-
 My Data Is Safe, Right?
My Data Is Safe, Right?There are two parts to the online safety conversation: privacy and security. Our quiz will help determine whether you're good to go on both fronts.
By Rachel Tobac Published
-
 Who Are Myka & James Stauffer, Who Face Controversy After "Rehoming" Son Huxley?
Who Are Myka & James Stauffer, Who Face Controversy After "Rehoming" Son Huxley?YouTube star Myka Stauffer and her husband James are facing backlash for re-homing their young son, Huxley, who they adopted in 2017 and who has autism.
By Jenny Hollander Published
-
 What Is "Houseparty," the App People Are Obsessed With In Quarantine?
What Is "Houseparty," the App People Are Obsessed With In Quarantine?It's the opposite of social isolation...without leaving your couch.
By Jenny Hollander Published
-
 Group Video Chat Apps to Download While You're Social Distancing IRL
Group Video Chat Apps to Download While You're Social Distancing IRLWho's up for a virtual game night?
By Jenny Hollander Published